“REAL ID offers us a false sense of greater security at the cost of taking a gigantic step toward making America a police state."
Former Congressman and Presidential Candidate Ron Paul
There is no question that the election system in Washington state is one of the worst in the nation. The most secure voting method is local, in-person voting with paper ballots and multiple checks. Instead, Washington uses automatic voter registration with almost no checks for non-citizens and all mail-in voting with almost no checks for who is actually filling out the ballot. Equally bad, Washington uses insecure voting machines that are easily hacked to remotely change vote results and insecure “Omniballot” online vote curing processes that violate both state and federal election laws prohibiting online voting. I have for many years written reports criticizing nearly every aspect of the election process here in Washington state.
But nothing in our current election system is anywhere near as dangerous as becoming part of a centralized Real ID national database system. Using this mega database, all 50 states and the federal government would share access to a vast national database that include images of birth certificates, marriage licenses, divorce papers, court ordered separations, medical records, and detailed information on the name, date of birth, race, religion, ethnicity, gender, address, telephone, e-mail address, Social Security Number and other personal data for more than 250 million Americans with no requirements or controls on how this database might be used. In this article, we will review just a few of the many reasons that a centralized national database will make our elections less secure.
The three primary computer security sources for this article are
(1) A 2007 61 page report written by 24 of our nation’s leading computer security experts which you can read here: https://archive.epic.org/privacy/id_cards/epic_realid_comments.pdf
(2) a 38 page 2008 report from the Electronic Privacy Information Center (EPIC) which you can read here: https://archive.epic.org/privacy/id_cards/epic_realid_0508.pdf
(3) An 8 page 2019 report from the Electronic Privacy Information Center (EPIC) which you can read here: https://archive.epic.org/apa/comments/EPIC-Comments-DHS-REAL-ID-June2019.pdf
Benefits of a Decentralized Locally Controlled Database System
Currently, Washington state voter registrations are handled locally by each county. They can communicate with and share data with other counties but typically only in pairs with one county auditor talking directly to another county auditor. They can also contribute to a state database. But each county retains control over their own data and each county has their own security processes with their own access rules and systems of locks and keys.
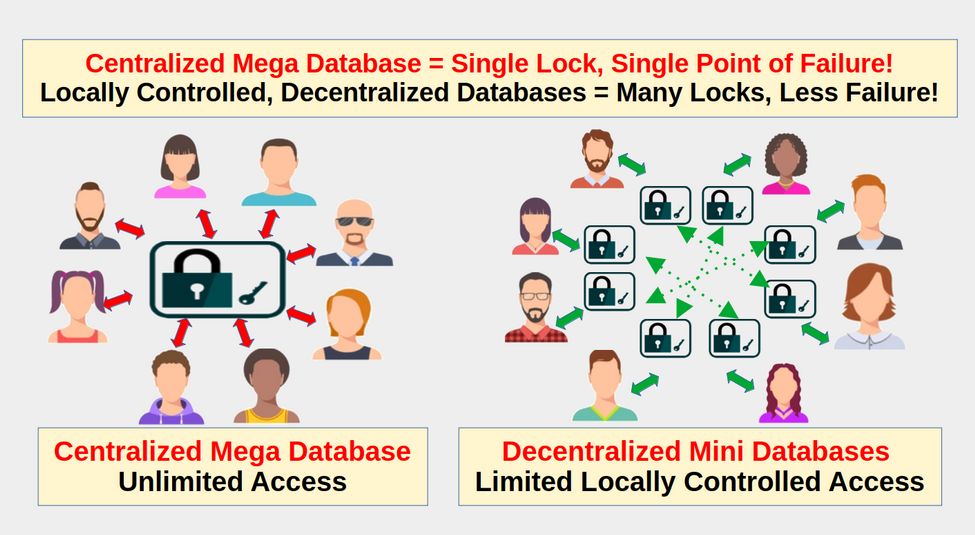
Danger of a Centralized Government Controlled National Mega Database System
Real ID (aka “enhanced” drivers licenses”) are still registered in each county. But the county database must be connected to the national Real ID system which allows any election agent in the nation to access the county database. Instead of isolated local databases, Real ID creates an interlocking combination of databases which in turn becomes a single mega data base with a single key used by everyone and thus has a single point of failure where any mistake by any election agent can compromise the entire election system.
How does Real ID work and why do people hate it so much?
For many citizens, the problem is not the additional $180 for 8 years for a Real ID (enhanced) Drivers License. Rather, it is the fact that the Enhanced License comes with a Radio Frequency Identification (RFID) chip that will remotely signal police to pull up your biographic and biometric data. Radio Frequency Identification (RFID) is a wireless technology that stores and retrieves data remotely. An RFID system includes four components:
#1: An RFID tag with a microchip (an Ultra High Frequency radio transmitter).
#2: An antenna embedded into the Enhanced Drivers License
#3: An RFID signal reader (a radio receiver)
#4 A centralized nation-wide government controlled database
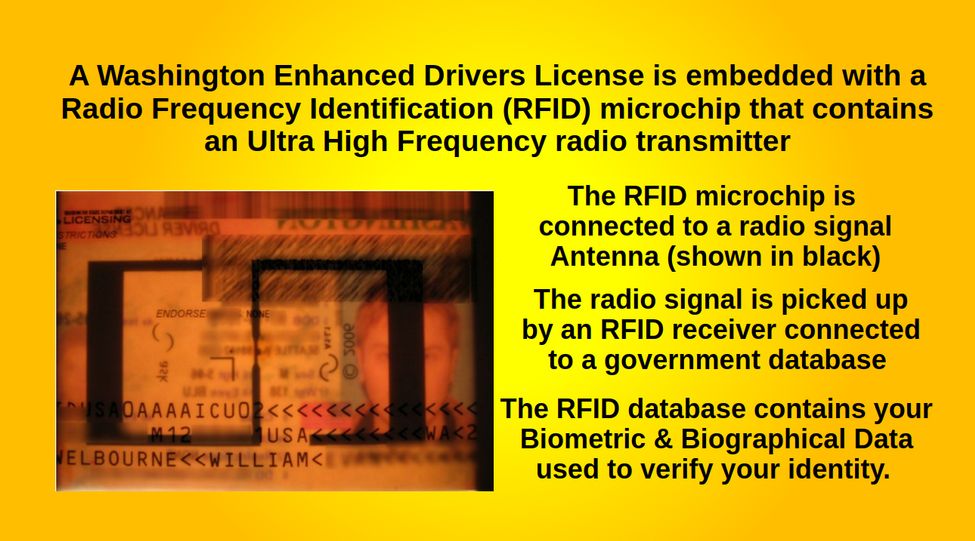
How the Radio Frequency Transmitter works
The RFID microchip embedded in your Enhanced Drivers license is programmed with a unique reference number that is connected by a database to your biographical and biometric data. At the border crossing, the police use an RFID radio receiver to obtain your unique the number. The border agent then transmit this number to the Border Protection network. The network compares the reference number to government records and sends your biometric and biographical information back to the Border Patrol agent who then uses that information to ask you a series of questions to confirm that your information matches with the information in the government database.
Your personal information will be unencrypted and thus can be read by anyone with an electronic card reader
The Real ID data transfer system requires that all “enhanced” driver’s licenses have an unencrypted “machine-readable zone” that would contain personal information on Americans that could be easily “skimmed” by anybody with a card reader. The unencrypted information contained in a Real ID card’s machine-readable zone can be read by anyone with an electronic reader. RFID chips emit a short-range radio signal containing information that identifies each chip. With RFID chips installed in Real ID cards, the government, business sector or even individual criminals could capture someone’s personal information and track his or her movements remotely without the individual’s knowledge.
Why Government controlled Biometric data will not provide security
Biometrics is a technology that identifies a person through his or her physical attributes, such as fingerprints, facial features, iris patterns or DNA. In 2007, Chris Paget of San Francisco, California, showed that RFID information could be pulled from a US passport card by using only $250 worth of equipment. This suggests that with the information captured, it would be possible to clone such cards. So why are they still being pushed?

Many Computer Data Security Experts warned against using RFID radio signals
There are significant privacy and security risks associated with the use of RFID-enabled identification cards. Both the Department of Homeland Security’s Data Privacy and Integrity Advisory Committee and the Government Accountability Office cautioned against the use of RFID technology in identification documents.
Many of our nation’s leading security experts made clear that RFID should not be used for human identification. DHS not only ignored these warnings, but they also ignored frequent warnings against leaving bar code personal data unencrypted.
Privacy and security risks associated with RFID-enabled identification cards include “skimming” and “eavesdropping.” Skimming occurs when an individual with unauthorized RFID reader gathers information from an RFID chip without the card holder’s knowledge. Eavesdropping occurs when an unauthorized individual intercepts data as it is read by an authorized RFID reader. RFID tags are remotely and secretly readable. RFID tags can be read from 70 feet or more, posing a significant risk of unauthorized access.
Lack of Encryption is a huge security risk
The Real ID network requires the use of a two-dimensional bar code, but does not require the use of encryption. The Department of Homeland Security’s own Privacy Office has urged the use of encryption in REAL ID cards. In its Privacy Impact Assessment of the draft regulations, the Privacy Office supported encryption “because 2D bar code readers are extremely common, the data could be captured from the driver’s licenses and identification cards and accessed by unauthorized third parties by simply reading the 2D bar code on the credential” if the data is left unencrypted.
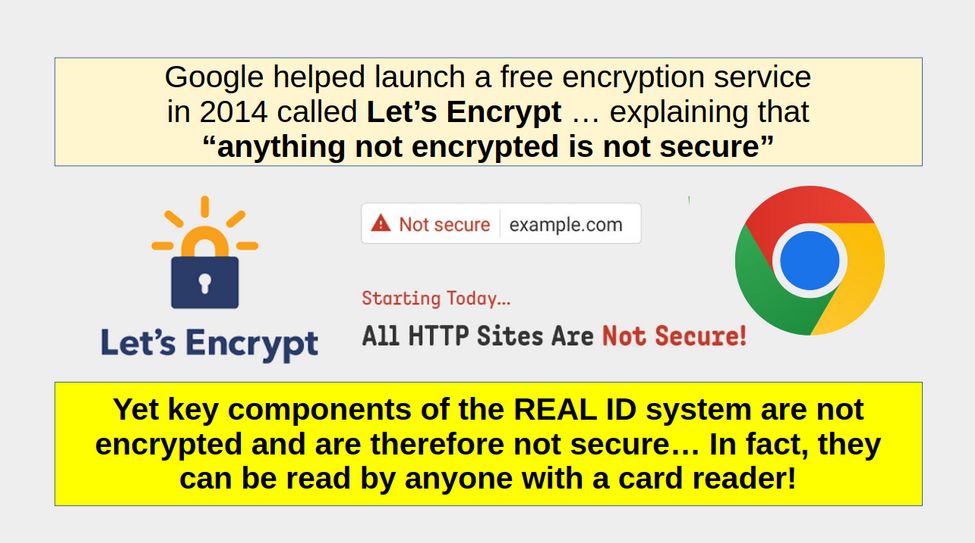
This risk is not theoretical, the DHS Privacy Office says, because “readers for the 2D bar code are readily available for purchase on the Internet at a very low cost, which permits unauthorized users to skim the information.” Such skimming is done without a person’s knowledge or consent.
The Real ID Act Violates Americans’ Privacy Rights
A central principle of computer security is that you can not have security without protecting privacy and you can not have privacy without protecting security.

Think of the keys to your home. If the keys do not keep out robbers, then you lose both security and privacy. Computers store our data. If computers do not keep out hackers, then our data has no privacy or security.
The Real ID Act poses one of the greatest threats to Americans’ privacy rights in this nation’s history. These problems are based on the design of the card, the information required to be stored on the cards, and the lack of safeguards for the personal data contained in the underlying interconnected databases
Every person applying for a Real ID card must be subject to a “facial image capture” and the photo must be stored in the motor vehicles database. If no card is issued, then the digital photo will be stored for a minimum of five years. If a card is issued, then the digital photograph will be stored for two years after the expiration date of the card (which can be up to 10 years).
States must capture digital images of all source documents presented by the applicants and store them in a transferable format for at least 10 years. Paper copies of the identification documents used to prove eligibility for a Real ID card must be retained for at least seven years.
Nearly 80 years ago, Supreme Court Justice Louis Brandeis described the “right to be let alone” as “the most comprehensive of rights and the right most valued by civilized men.”
The Real ID Act effectively rescinds the right to be let alone. It creates an infrastructure that allows the government to consolidate the oceans of personal data into a single network accessible by government employees throughout the country. It creates an enormous electronic infrastructure that government officials, and private corporations can use to track law-abiding Americans’ activities and movements.
Nor will the information contained in the Real ID database be limited to a person’s driving records or even to the source documents needed to obtain a Real ID license. The authors of the Real ID Act deliberately put no limits on what information can be stored in this national database. This means future administrations will be able to include additional information such as an individual’s travel records or gun ownership.
The Real ID System increases the risk of Identity Theft
This national mega-database will invite government snooping and be a goldmine for identity thieves. A centralized system of identification creates a “one-stop shop” for identity thieves. Centralizing authority over personal identity into one database and one card increases both the risk of identity theft as well as the scope of harm when it occurs.
Identity theft is a widespread and growing problem in the United States. It is the most widely reported type of consumer fraud. The number of identity theft complaints increases every year - and the FTC warns that the vast majority of identity theft cases are never reported. In one study, the agency concluded that nearly 8.4 million people, or 5 percent of U.S. adults, were the victims of identity theft.
Security analysts warn that the Real ID Act will lead to more cyber-crime by creating one nationwide database of sensitive personal information. Eugene Spafford, chairman of the policy committee of the Association for Computing Machinery, warned that the Real ID Act creates the potential for identity theft in an unprecedented level. He cites the huge potential for human error, fraud and security holes.
The consequences of identity theft would be more pronounced under a Real ID regime. Thieves with access to the Real ID mega-database could make copies of birth certificates or Social Security cards, making it difficult for victims to recover their identities.
The Real ID database network would be particularly vulnerable to thieves because it would have hundreds of access points across the country. Its tremendous size would also increase risks of human error and abuse. Information stored in the database would only be as secure as the state or DMV office with the weakest security system or least trustworthy staff.
The Security of the Real ID system is only as secure as the State DMV office with the weakest security
Because any election official in any state will have access to the voter information of any person living in any other state, the birth certificate or Social Security number of someone who lives in Seattle will be accessible to DMV clerks in Florida, Texas or Oregon.

The problem is that government officials have a poor track record for being trustworthy. In recent years, scores of DMV employees nationwide have been implicated in schemes to sell fraudulent licenses and data to identity thieves. Consider the following examples:
The entire 11-person staff of a DMV office in Newark, N.J. was fired in February 2003 after investigators determined fraud was so rampant that no one in the office could be trusted. That incident was part of crackdown on corruption throughout New Jersey’s DMV system that produced more than 100 arrests and the firing of the top managers of 28 of the state’s 45 DMV offices.
In Connecticut, six former DMV employees were convicted on corruption charges for selling thousands of driver’s licenses to criminals and undocumented immigrants between October 2003 and March 2004. An accomplice testified in court that people paid as much as $3,000 for a fraudulent license.
In 2008, on the day that DHS released the final regulations for REAL ID, “A Maryland Motor Vehicle Administration employee [...] and four others were indicted [ ] on charges that they made and sold fake State driver’s licenses and identification cards in exchange for money.”
Large-scale data breaches have occurred in State DMVs across the country; if the databases are linked under REAL ID, these breaches will only grow in scale.
In 2005, the Oregon DMV lost half a million records. Also in 2005, in Georgia, a dishonest insider exposed 465,000 records.115 In 2011 a North Carolina DMV worker was charged with five counts of identity theft after she used DMV computers to obtain information to take out payday loans in other people’s names.
In 2014, the California DMV suffered a data breach where credit card information was compromised via their online payment system.
In 2015, an Oregon man was able to download a list that contained a DMV list of identification numbers as well as federal income tax forms and was charged with 26 counts of aggravated identity theft.
Also in 2015, the U.S. Voter Database was breached. In the largest government data breach to date, a database of 191 million voters was exposed. The problem came down to human error. The database was incorrectly configured and exposed on the Internet. It contained the personal information – names, dates of birth, party affiliations, emails, addresses, and more – of all registered voters in all 50 states.
Also in 2015, the Office of Personnel Management exposed 21.5 million records: Hackers stole the information of 21.5 million former and current US government employees.
Also in 2015, the Georgia Secretary of State exposed 6 million records: A massive data breach occurred when Brian Kemp’s office released data, including personally identifiable information, to political parties, the media, and other subscribers who buy voter information (legally) from the state.
In 2016, the Department of Homeland Security database was hacked. An anonymous hacker claims to have stolen more than 200GB of files from the Department of Homeland Security, including the names and contact information of more than 30,000 employees. A database containing 22,174 names, job titles, email addresses, phone numbers and other location information was posted to Cryptobin.org this afternoon. A separate list of 9,371 similar records was posted yesterday.
In 2017, the personal information of almost 200 million registered voters was leaked, data owned by Republican data analysis group Deep Root Analytics. The data was first discovered by the cyber threat analysis team at UpGuard, which was the largest exposure of sensitive voter information in history.
Also in 2017, the California Secretary of State exposed 19.2 million records: Voter records for more than 19 million people were available for all to view after a database was left unprotected.
In 2018, the US Postal Service saw 60 million records exposed due to a flaw in storing users’ account details – something USPS was warned about a year prior.
Also in 2018, the Government Payment Service exposed 14 million records: GovPayNow.com, which is used by thousands of local and state governments, leaked over 14 million customer records, including names, phone numbers, addresses, and the last four digits of the payer’s card.
In 2020, a group of thieves responsible for collecting millions in fraudulent small business loans and unemployment insurance benefits from COVID-19 economic relief funds gathered personal data on people and businesses they were impersonating by leveraging several compromised accounts at a little-known U.S. consumer data broker.
In 2022, an FBI program called InfraGard was hacked. Intended to build cyber threat information sharing partnerships with the private sector, its database of contact information on more than 80,000 members was hacked and put up for sale on an English-language cyber crime forum.
In 2023, two U.S. men were charged with hacking into a U.S. Drug Enforcement Agency (DEA) online portal that taps into 16 different federal law enforcement databases. Both are alleged to be part of a larger criminal organization that specializes in using fake emergency data requests from compromised police and government email accounts to publicly threaten and extort their victims.
Since 2014, the US government has suffered 1,283 breaches affecting more than 200 million records. Based on the average cost per breached record (as reported by IBM each year), we estimate these breaches have cost government entities nearly $30.4 billion
In May 2025, a cyber security firm issued a report on attacks during the first quarter of 2025. The first quarter saw 876 new breach notifications representing 658 distinct security incidents that impacted over 32 million people. Here are the locations of the data breaches so far this year:
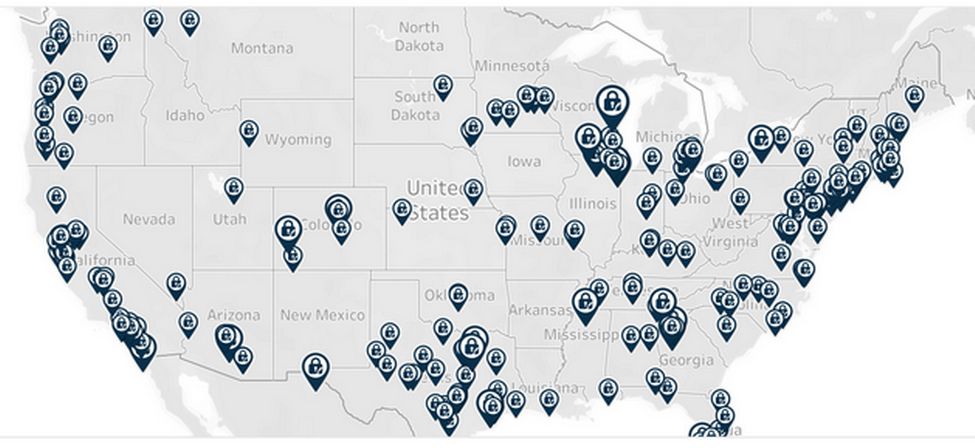
Criminal hackers compromised the authenticating documents in state DMVs including Oregon, North Carolina, and California.
A 2004 survey found that 23% of Californians say they have not registered to vote because they want their information to remain private.
https://www.calvoter.org/issues/votereng/votpart/surveyresults.html
Given the lousy track record of government agencies in protecting voter data, why would anyone want to make things even worse by creating a mega database that could be accessed by thousands of government agents?
Real ID creates a massive database network that will make our personal information easily available to thousands of federal government bureaucrats in all 50 states. Government officials can and will abuse this system.
Four Presidents opposed a centralized national database
The national database scheme was opposed by the Nixon administration, the Carter administration and the Reagan administration. Ronald Reagan referred to the scheme as the “mark of the beast.”

The Real Reason for Real ID: Follow the Money
In 2020, the world RFID market was worth US $12 billion, up from US $7 billion in 2012. This figure includes tags, readers, and software/services for RFID cards, labels, fobs, and all other form factors. The market value is expected to rise to US $16 billion by 2029.
What’s Next?
It is bad enough that the Proof of Citizenship Initiative will disenfranchise thousands of legal voters, and violate the privacy rights of millions of Americans – all while making our election system less secure. But it also violates several federal laws and therefore is certain to be tossed out in federal court should it make it past the voters. The legal problems of this Initiative are the subject of our next article.
